The Intent Breakthrough: Redefining Email Security with a new category of Intent-Based Detection™

Introduction
For nearly two decades, email security has rested on a linear assumption:
if a security engine can reach the landing page, decode the redirect chain, reconstruct the URL path, or detonate the attachment, it can adjudicate risk.
That operating premise no longer holds.
Modern evasions have removed the inspection layer entirely, and AI-generated phishing has industrialised syntactic variation to the point where payload-visible detection is structurally obsolete.
This discussion serves a singular purpose: to establish Intent-Based DetectionTM as the only durable foundation; a new category of threat detection for modern email defense, not as an evolutionary upgrade, but as a fundamental replacement.
The Neural Analysis and Correlation Engine, NACE™, was designed precisely on this first-principles shift.
Evasion as Architecture, Not Tactic:
Phishing no longer hides in detail – it hides in access.
The payload, credential page, and infrastructure state are now gated specifically against scanners, crawlers, and automated simulators.
As per the current email threat-landscape that we see in our day-to-day telemetry across customers; Evasion today is not decorative (just limited to obfuscation) – it is the environment:
- CAPTCHA walls positioned before credential harvest (Exhibit A)
- QR-mediated bypass into legit-services where domain reputation fails (Exhibit B)
- Disposable domain chaining and self-expiring cloud objects (Exhibit C)
- Interaction-gated rendering that activates only after human movement signals (Exhibit D)
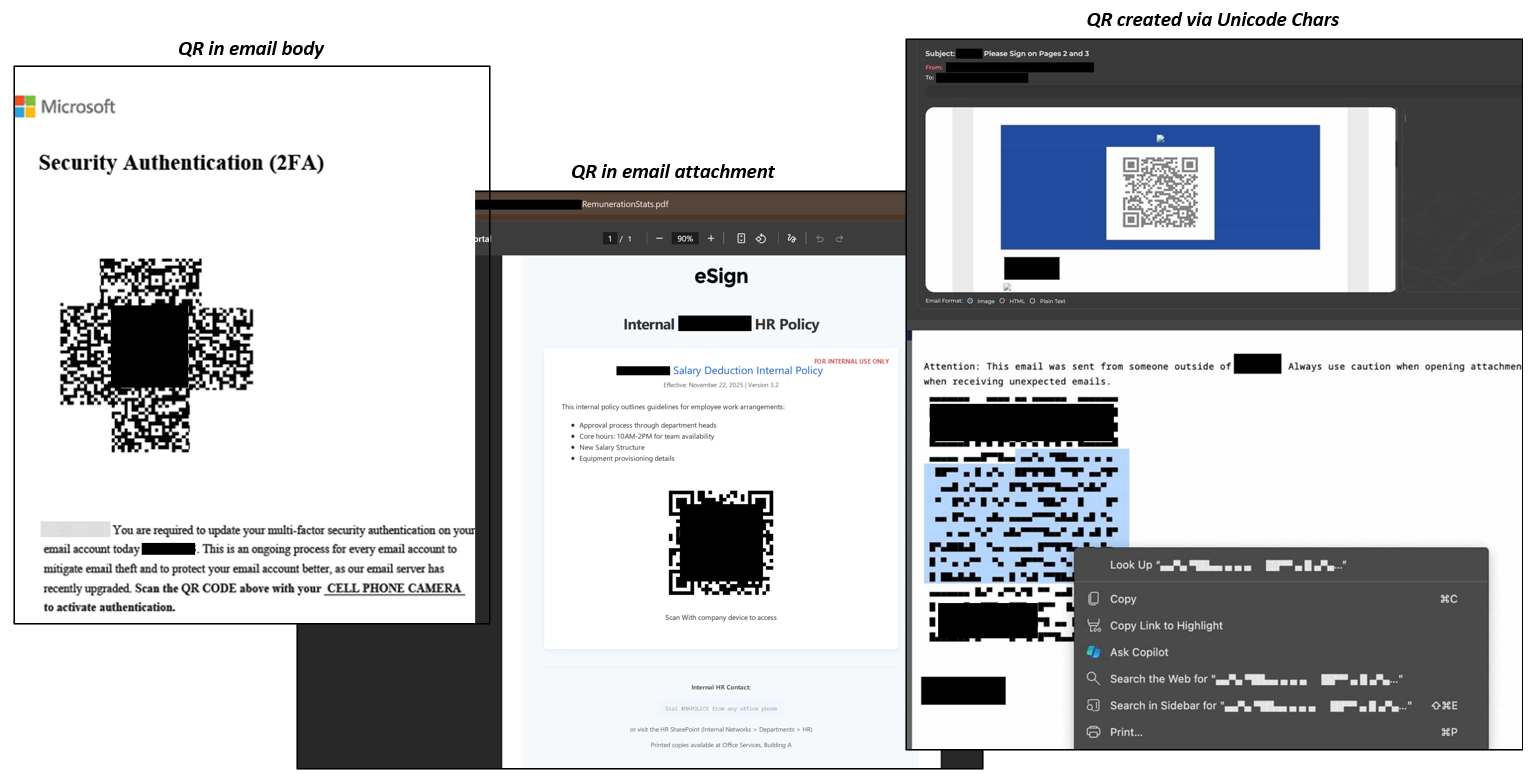
Exhibit A: Unique CAPTCHA gating used to prevent conventional scanners from accessing the landing environment
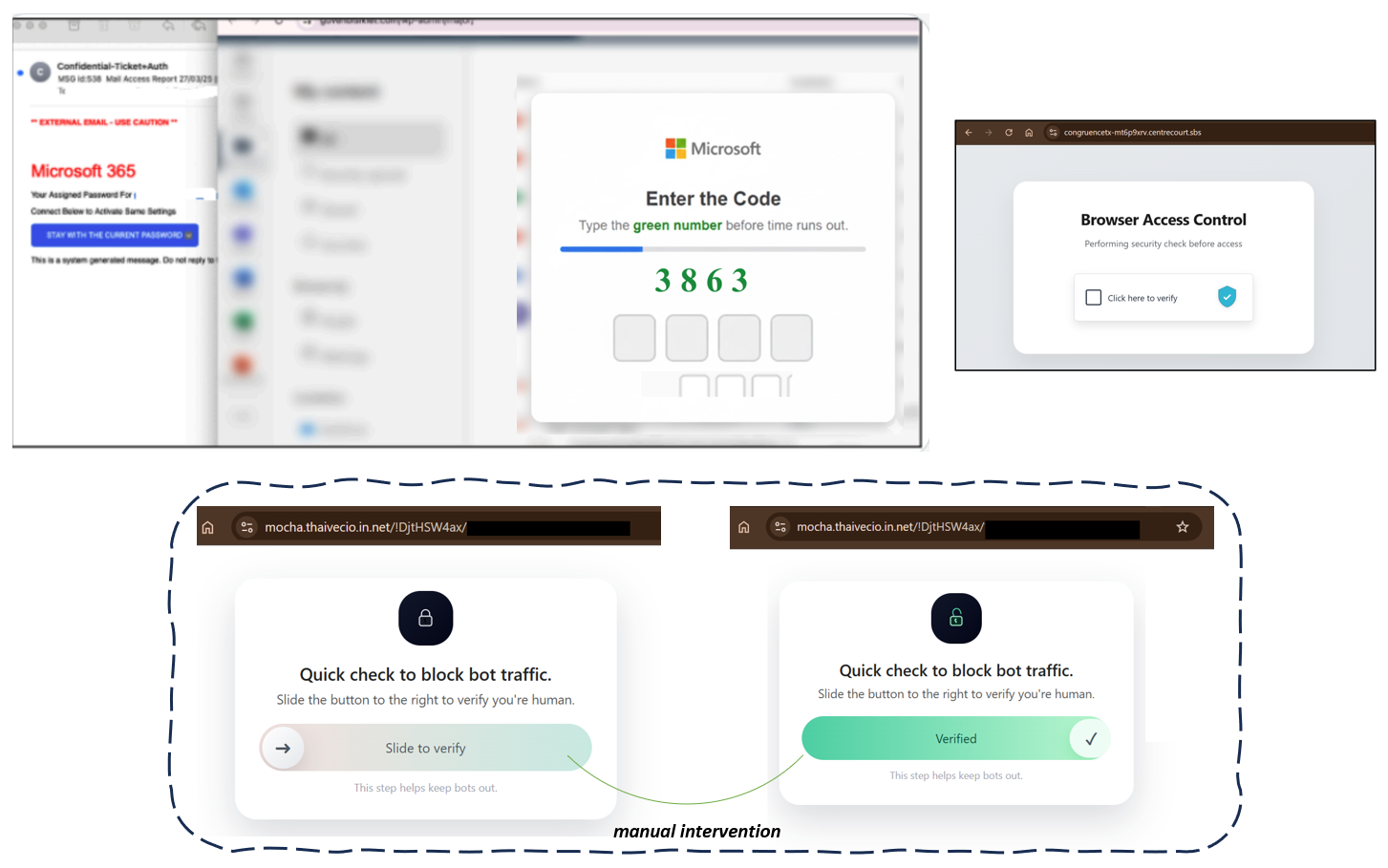
Exhibit B: QR-initiated detour through a legitimate service layer used to bypass email-layer inspection and deliver credential capture on the user’s device

[Exhibit C: Disposable domain chaining used to rotate redirection hosts and prevent security systems from reaching the final credential page]
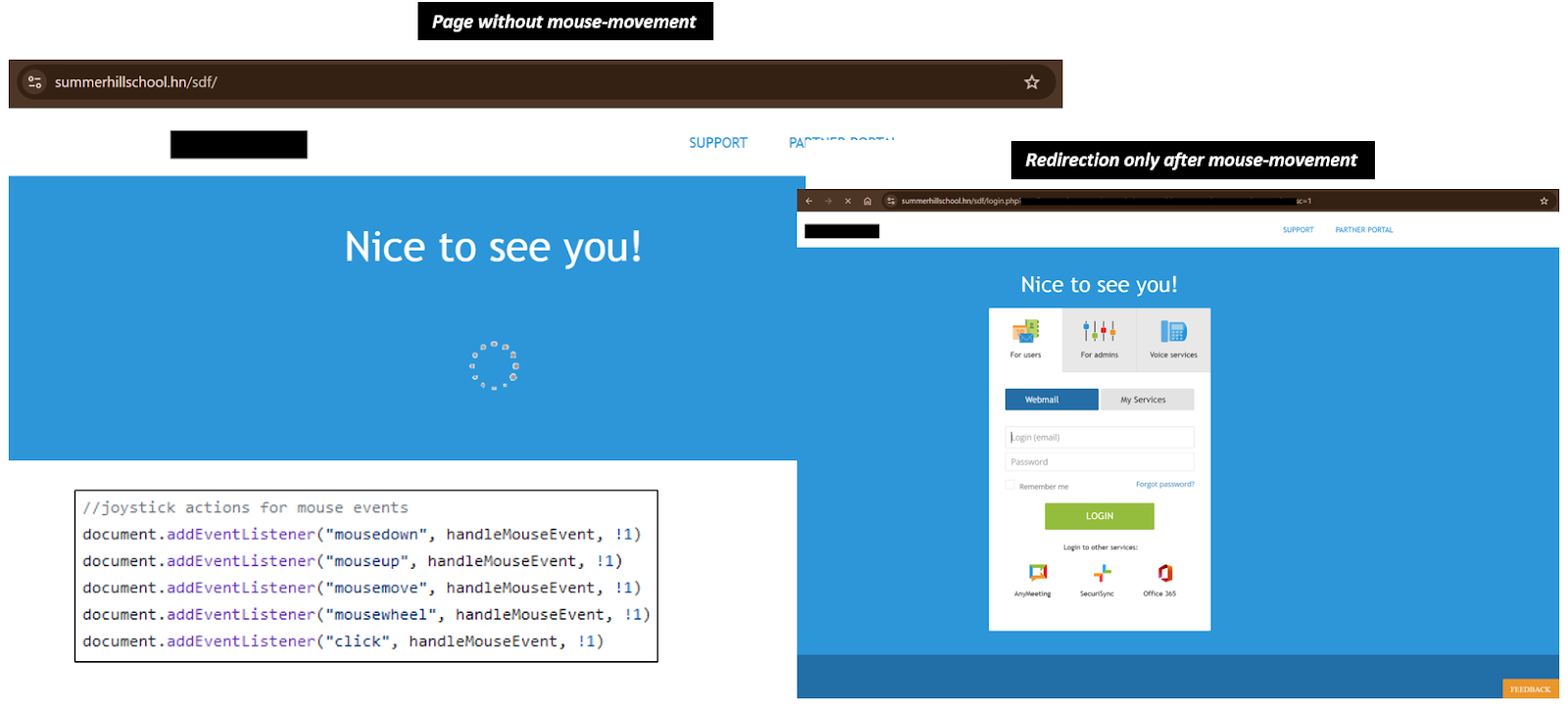
[Exhibit D: Human-interaction gating used to withhold redirection until mouse-movement signals are detected, disabling automated crawler access]
Legacy security frameworks were built to observe.
Modern adversarial design ensures there is nothing observable.
Intent-Based Detection does not require the payload to reveal itself. That is the point of divergence.
AI Is Not Just Accelerating Threats—It Is Multiplying Linguistic Surfaces
Generative AI has not improved phishing; it has made it endlessly rewritable.
Industrial-grade malicious toolsets such as WormGPT, GhostGPT, DarkLLM, FraudGPT, and now low-cost platforms like DeepSeek have shifted the sophistication curve.
Attackers can now:
- create thousands of BEC impersonation narratives, each semantically equivalent and syntactically distinct
- adjust tone, geography, linguistic register, and role in seconds
- iterate CTA designs specifically to escape language-pattern classifiers
- generate multilingual corporate authenticity at publishing quality
Traditional NLP classifiers fail not because they are imprecise, but because they are bounded.
Supervised binary and multi-class models degrade when exposed to semantically consistent but syntactically infinite variants; an unavoidable consequence of out-of-distribution mutation.
A First-Principles Shift: Intent Before Artifact
NACETM, Intent-Based Threat PreventionTM, AI Platform eliminates payload dependency by design.
It evaluates communication meaning, not exploit accessibility.
Inference and reasoning architecture operates on deriving intent:
- semantic extraction across body, subject, and attachment text
- thematic clustering and hierarchical topic modelling
- isolating purpose of email from similarity analysis and semantic re-ranking
NACE™, then conducts contextual reasoning [1][2][3] across the email’s intent, SMTP-header features, attachment characteristics, and call-to-action URLs enables NACE™ to derive a malicious verdict without relying
- on landing-page analysis for phishing,
- exploitation-stage features for malware,
- user-behavior analytics, relationship graphs for BEC.
Attackers can rotate URLs, hosts, redirects, and delivery paths indefinitely.
What they cannot rotate is objective.
This is the invariance of NACETM exploits.
NACETM does not chase the exploit. It determines why the email exists.
The Executive Inflection: Why Leadership Must Rethink the Model
CISOs, CTOs, and product architects are not facing incremental complexity; they are facing structural displacement.
- Payload invisibility is no longer an anomaly;
- It is the adversary’s primary feature and is using AI tools like FraudGPT, Evil GPT etc to scale.
NACETM 3.0 implementation of Intent-Based Threat PreventionTM category to eliminate the advantage created by disappearing payloads. When the threat verdict no longer requires landing-page access, QR traversal, CAPTCHA circumvention, or attachment detonation, the evasive layer becomes irrelevant.
This is not forecasting tomorrow’s threat model.
This is the operational necessity for current-state AI adversarial design.
Final Perspective
Generative phishing has eliminated inspection.
NACETM implementation of the new category of Intent-based Threat PreventionTM eliminates dependence on inspection.
By elevating semantics, thematic signalling, derived intent for contextual reasoning over above payload visibility, infrastructure accessibility and execution artefacts, analysis NACETM forms a new detection perimeter.
The attacker can obscure the route, infrastructure, and exploit itself. They cannot be obfuscated is the purpose of the communication.
In the era where landing pages disappear, URLs self-erase, attachments morph, and syntactic space becomes infinite, intent is the only durable detection surface.
NACETM is built upon that recognition—not to improve the old model, but to redefine its replacement.
Learn more about how NACETM protects against phishing and malicious URLS, whether created by human threat actors or powered by AI, here.
References
[1] Intent-Driven Contextual Reasoning Across Email Conversations: Announcing NACE™ 3.0
[2] Harnessing Language Models to Stop Evasive Malicious Email Attachments/URLs
Dec 5, 2025 7:50:18 PM
